- Windows 10 Home Vs Pro
- Windows 10 Home Product Key
- Rdp Windows 10 Home Hack
- Does Windows 10 Home Support Remote Desktop
The RDP Wrapper Library (rdpwrap) project hot-wires Windows’ built-in RDP server (the Terminal Service) so you can start it even on Windows 10 Home. It also adds the required rules to the Windows Firewall to allow remote RDP connections to your PC. Unfortunately, Remote Desktop feature is not available in Windows 10 Home, it can only be enabled on computers running Windows Pro, Windows Enterprise and Windows Server. Although, Windows 10 Home is equipped with Remote Desktop Client Software, it lacks the propriety RDP server from Microsoft, required for accessing remote computers. Like previous versions of Windows, Windows 10 Home offers a client for connecting to Remote Desktop servers, but not the Remote Desktop server itself. To host a Remote Desktop server using Windows 10’s built-in Remote Desktop feature, you’ll need Windows 10 Professional. In Windows 10 Home editions, the incoming remote desktop connections are forbidden at all (you can solve this only using the RDP Wrapper Library). Only one simultaneous RDP connection is supported. When you try to open a second RDP session, the user is prompted to close the existing connection.
Hello, I am cedrozor the author of Myrtille, a project that started in 2007 as a challenge for fun with former work colleagues, on our spare time. The goal was to provide a native web access, for a simplified user experience, to remote servers and applications. We wanted legacy desktop applications to be as easy to use as a website, accessible from a single URL, making them literally “web apps”.
It was originally the idea of UltraSam, the author of UltraVNC (another well known open source project), who was before that my project manager in a teleconferencing company based in France. But instead of the VNC protocol, we focused more on RDP because the rest of the team (including me) was more into .NET/C# development and we wanted something new in the Windows environment. That said, Myrtille relies on an abstraction layer and could easily integrate VNC or any other protocol (as it was done with SSH).
We started with RDesktop, but moved quickly to FreeRDP when it was released! :)
I have tried to keep the Myrtille footprint into FreeRDP as minimal as possible. Myrtille communicates with FreeRDP through named pipes (IPC), in order to maintain a FIFO data transfer. User inputs (keyboard, mouse, touchscreen, etc.) are captured by the browser (using javascript) and forwarded through the RDP session, while display updates (regions of the screen that have changed) are compressed into PNG, JPEG or WEBP images and sent to the browser (using websocket, server-sent events (HTML5) or even long-polling (HTML4)).
Because FreeRDP is a big project, I wanted an easy way to track the Myrtille code within it (whenever I couldn’t have it into separate files). Thus, all the Myrtille code is surrounded by “#pragma region Myrtille” and “#pragma endregion” tags. This is very handy when I need to resynchronize the Myrtille fork of FreeRDP with the FreeRDP repository! Because, of course, I want Myrtille to benefit from the latest features, optimizations and bug fixes from FreeRDP! :) in this process, I may also find and fix bugs in FreeRDP, then inform the FreeRDP team.
In an earlier version (0.9.x), The Windows FreeRDP client (wfreerdp) was written in C++. It’s possible to mix C and C++ code in a single project, so I was able to keep most of the code I wrote years ago and benefit from some C++ improvements over C (OOP, GDI+ image processing, etc.).
I also wanted to have a clean separation of concern between Myrtille and FreeRDP, so each RDP connection spawns a FreeRDP process. This makes it easier to track all active connections and if necessary disconnect one by killing its process.
From the start we decided that we didn’t want any plugin, extension or whatsoever in the browser. It would be a pure HTML/JS/CSS implementation. We also wanted to avoid javascript libraries whenever possible (and reasonable), to avoid useless (and countless) dependencies and keep the code low profiled. For simple tasks (and Myrtille doesn’t require/do anything fancy), I think it’s fine (and even good) to simply use vanilla javascript. Javascript is a powerful language, constantly evolving, and I have fun learning and harnessing it. I’m also a minimalist person who loves to get its hands dirty in the engine to see how things work on a lower level! :p
It was even more difficult back in time (2007), because websockets and canvas (HTML5) weren’t available. We had to rely on XmlHttp requests, long polling and divs (HTML 4), with of course different implementations in different browsers (no typescript back then). IE was still widely used at this time, so we wanted our PoC to run on the first version that supported XmlHttp, namely IE6 (to add even more difficulty!).
That said, that was before SignalR was available to abstract and simplify network communication (automatic and transparent switching of protocols in case one of them is not available or fails). If Myrtille were to start today, I would of course make use of it (in addition to a few other libraries). Another thing I would do would be to use .NET core and the latest new stuff, in order to take Myrtille forward in the future and also have it on multiple platforms (using xfreerdp on Linux, for example). This is planned in fact, and I could use some help for it (any contribution is welcome!). Another option would be to have a commercial version of Myrtille, with a paid license to support these developments (because it’s a lot of work and I now have to earn a living, as an independent developer).
Among the upcoming features, file transfer is the next improvement goal. Microphone support is also planned. Maybe also smart cards after that. A separation of the Myrtille gateway and services is also planned, for an easier configuration of the gateway into a DMZ, and further enhance the security (the installer will allow to select the module to be installed; currently this must be done manually). Still about security, I would like to offer another 2FA out of the box (probably Google Authenticator).
Regarding the user interface, I think Myrtille also needs a little visual rework. The login page, the toolbar will be redesigned with better flat styles, colors and icons.
About deployment and integration (and devops by extension), I would like also to bring more cloud support to Myrtille; Azure obviously, because of its integration within the Microsoft/Windows ecosystem, but not only (Amazon, Google, etc.). Myrtille already have a Docker image, but there are some limitations regarding print and audio. I will also look into that.
Responsiveness is the key to a good user experience. I tried hard to chase for every millisecond I could save in the roundtrip workflow. That’s also why I wanted a lightweight javascript code from the start. The Myrtille gateway is also just that, a link between the browser and FreeRDP, maintaining the correlation between the http and rdp sessions, receiving/forwarding data from/to both sides.
Whenever possible, I try to parallelize the processing. The user inputs and display updates, for example, are asynchronous. You can have a display change resulting from a user action, or not. What is important however, is to maintain the order in which they occur. I decided to use named pipes between the gateway and FreeRDP, because they are FIFO queues and maintain such an order. XmlHttp requests and websocket messages are also delivered in order, and so are long polling DOM injections and server-sent events (SSE).
A path for improvement would be to use hardware accelerated graphics and take advantage of the H.264/AVC encoding supported by FreeRDP. Myrtille actually relies on images (PNG/JPEG/WEBP), generated by GDI+ (win32 API, software), but this could be replaced by a video stream (MP4/OGG/WEBM, etc.), generated by FreeRDP (against hardware, or software when using a VM), and pushed from the gateway to the browser into an HTML5 <video> tag or handled by a modern web API (MediaSource, WebRTC, etc.).
Many thanks to the FreeRDP team for this wonderful project! It is not an easy task when working with such a complex protocol and with so many changes over the years.
If you want to know more about Myrtille and its offered services (support, training, etc.), watch demo/tutorial videos or get in touch, you can consult our website.

If you look closely at Windows 10 Home, you’ll find most of the components required to run the Microsoft RDP Server already installed as part of the operating system. Enabling the remote desktop server normally requires a PC running either the Windows 10 Professional or Enterprise editions. Here’s how you can also enable the RDP server in the Windows 10 Home edition.
Windows 10 Home Vs Pro
Before you set up an RDP server, you should be aware that exposing an RDP server to the internet is incredibly risky. RDP is a common vector for compromising Windows systems. There have been multiple security issues with Windows RDP servers in recent years.
Only install an RDP server if you absolutely need one. Configure a restrictive firewall to keep from being accessible from the internet. Only connect to your RDP server through an encrypted network bridge (e.g. a local VPN.)
Windows 10 editions that officially support the RDP Server feature can turn it on from the user interface in the Windows Settings app or the Windows System dialog: Properties: Remote. However, you won’t find these settings in Windows 10 Home or S editions.
The RDP Wrapper Library (rdpwrap) project hot-wires Windows’ built-in RDP server (the Terminal Service) so you can start it even on Windows 10 Home. It also adds the required rules to the Windows Firewall to allow remote RDP connections to your PC. Make sure all accounts on your PC have strong passwords to protect it against unauthorized remote logins!
RDP Wrapper doesn’t unlock Windows’ user interface for managing the RDP server. Instead, you can use the bundled RDPConf program which comes bundled with RDP Wrapper to manage these settings.
It’s easy to get set up with RDP Wrapper. Download the latest MSI installer and run it.
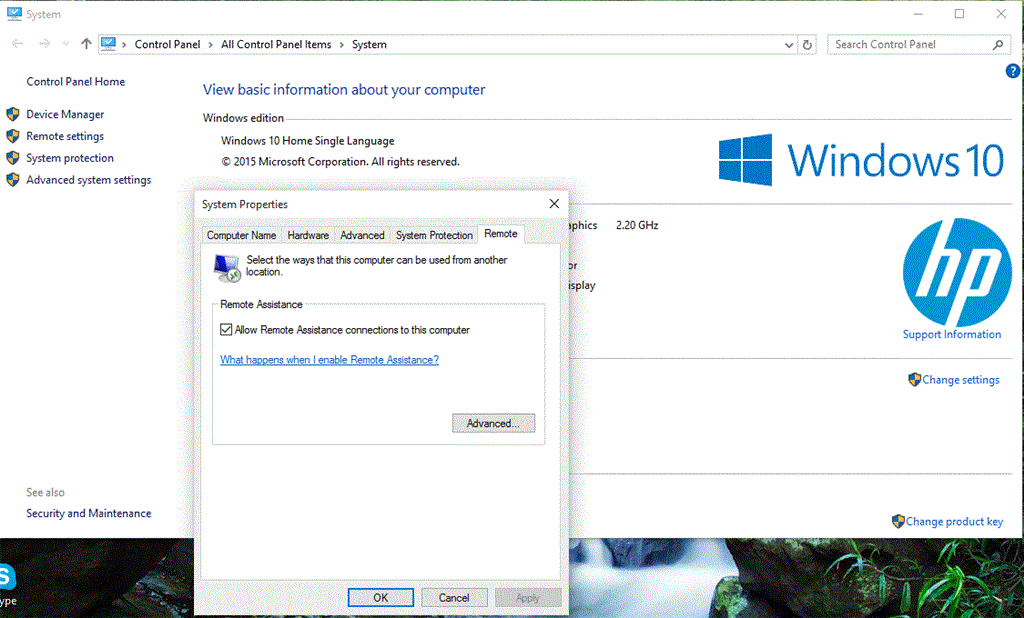

Alternative approaches to enable RDP in the Home edition of Windows often make alterations to Windows components that are difficult to revert and may cause problems later when the system updates through Windows Update. RDP Wrapper instead makes some minor adjustments to Windows configuration and uses existing Windows components and services to enable remote RDP access.
You can use the Remote Desktop Connect client to remotely access the desktop of a Windows PC running an RDP server. The Remote Desktop Connection client program is available in all editions of Windows including Windows 10 Home and Mobile. It’s even available on macOS, iOS, and Android through their respective app stores.
There aren’t any alternative third-party RDP server implementations available on Windows, so you must either use the implementation built-in to Windows or not at all. RDP is a proprietary protocol by Microsoft after all, so this may not be all that strange.
The Windows 10 Professional upgrade cost for a Home edition user is quite expensive, and it may be worth investigating alternatives like VNC. VNC is an open-source alternative remote desktop protocol. You’ll find plenty of free servers and clients available for all operating systems including Windows. VNC suffers from having many almost-but-not-quite compatible implementations, resulting in an ecosystem where not all clients work well or at all with all servers. I’ll not cover VNC any further in this article.
You may be wondering whether the Windows license allows for something like RDP Wrapper to lift limitation in the Home edition? Let’s take a quick look at the relevant parts of the Windows Operating System license:
Windows 10 Home Product Key
Disclaimer: I’m not a lawyer and this isn’t legal advice. This is just my reflections and interpretation from reading the Windows License.
You may argue that RDP Wrapper just enables you to take advantage of the functionality that you’re licensed to utilize by section 2.d(ⅴ), but section 2.c+2.c(ⅳ) contradicts 2.d(ⅴ) with no clear reading as to which one takes precedence. Section 2.d(ⅴ) doesn’t expressly grant an exception from 2.c+2.c(ⅳ), but 2.d(ⅴ) is more specific to the situation at hand.
I’d like to pause here to say the current Windows license text makes it clear that you’re not allowed to work around any problems and limitations imposed by Windows. Which means that you’re more than likely already violating the Windows license simply by installing any number of utility programs that extend or tweaks Windows functionality.
I.e., using the file search utility FileLocator to work around the restrictions Windows puts in place to limit your ability to find files on the system is strictly speaking a violation of the Windows license as written. Most of the third-party and even other Microsoft software you install will put you in violation of the Windows license.
The use of RDP Wrapper may be interpreted as an application of a method for circumventing digital rights management system and thus illegal under the Digital Millennium Copyright Act (DMCA) in the USA, and who-really-knows-what-is-illegal-in-different-member-states under the Copyright Directive (2001/29/EC) in the EU. This part of the license is, however, open to interpretation and I’d say Microsoft would be hard-pressed to apply it to any situation beyond attempts at circumventing their copy-protection and validation systems.
Not being able nor permitted to work around bugs and problems in Windows is one of the reasons why I choose Linux over Windows.
Rdp Windows 10 Home Hack
If you want to stay in compliance with the Windows license, you can either choose to use a free VNC alternative or upgrade your Windows 10 Home license to a Pro edition license by purchasing a digital upgrade code from Amazon.
Does Windows 10 Home Support Remote Desktop
